Using Cyber Simulation to Improve OT/ICS Security
Using Cyber Simulation to Improve OT/ICS Security
Organizations are increasingly integrating OT infrastructure with IT systems, allowing them to have a comprehensive view of the industrial ecosystem and equipment. That makes it easier to manage and oversee, but it can also increase the possibility of cyber threats. Security teams need to understand not only traditional cybersecurity tactics and procedures, but also OT-specific ones. Cyber simulation exercises designed expressly for OT/ICS security help cyber defenders be more effective and reduce risk.
What is OT?
Most of us are familiar with the term “information technology” (IT), which is typically associated with protecting data and networks. “Operational technology” (OT) is not as commonly known, but it is vital to enterprises and our critical infrastructure. OT is “hardware and software that detects or causes a change through the direct monitoring and/or control of industrial equipment, assets, processes and events,” according to Gartner.
In short, OT refers to the devices and systems that manage industrial operations, such as manufacturing equipment, oil & gas and electricity monitoring systems, or mining operations. If the OT ecosystem is threatened, the repercussions can be much worse than an IT-related breach. When OT systems go down, people can get physically – and even fatally – hurt.
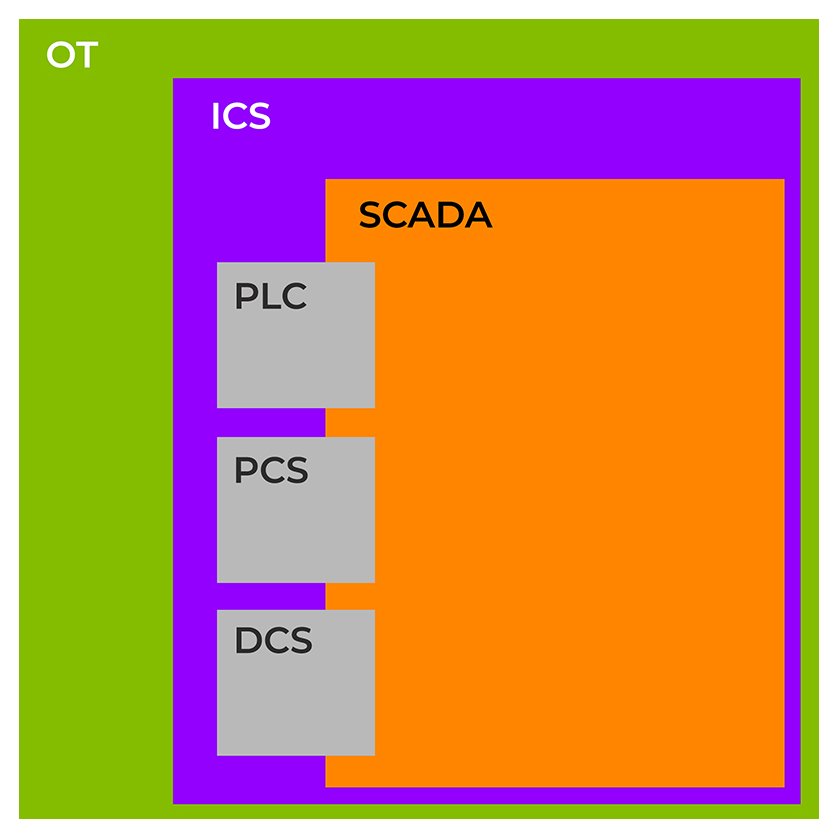
OT, ICS and SCADA
OT includes power grids, water systems, robotics, telecommunications, transportation networks and more. These systems are often critical to the functioning of society and, as such, they must be protected at all costs.
When they are breached, it goes beyond the digital realm made up of 1s and 0s – there is a tangible, physical result.
“Industrial control systems” (ICS) are used to manage and control these raw material and infrastructure systems and processes. ICS is a major subset of OT and, as such, the terms can be used interchangeably.
ICS uses systems architecture like “supervisory control and data acquisition” (SCADA) to manage and analyze data for large, complex systems. ICS systems also encompass programmable logic controllers (PLCs), process control systems (PCS), and distributed control systems (DCS).
Key Difference Between IT and OT/ICS Security
Because IT and ICS security are concerned with different things – digital versus physical actions – their objectives are different.
IT security is concerned with data and keeping it secure. It prioritizes confidentiality, then integrity, and then availability. That’s why the information security triad is sometimes referred to as the CIA triad. The goal is to make sure systems are not compromised and sensitive information is not leaked. IT cyber defenders are minimizing risk of data breaches, data destruction, and system downtime.
In contrast, ICS security prioritizes integrity and availability of processes and systems. Confidentiality is still valued, of course, but it is less critical in the OT space. The goal of ICS security is keeping people safe. ICS cyber defenders are reducing risk of critical infrastructure disruption, physical damage to engineering assets, negative impacts to the environment, injury and death.
The IT/OT Convergence
Since systems that used to be physical only are now computerized, OT is converging with IT. Refineries are a good example: Instead of having someone on-site to turn knobs, all of the temperatures, pressure levels, and other functions are monitored and changed without human involvement. Sensors communicate the status to a central facility, which analyzes the data and independently configures the controls for optimal performance. The technology can be overseen by someone in another city, state, or country.
This convergence can bring many efficiencies as technologies merge into one system and workflows are streamlined. Data handling and network protocols can be standardized, ensuring greater accuracy, smoother operations, and improved uptime.
It also means that OT systems can be hacked.
Cyber Simulation Training for OT/ICS Security
With OT and IT networks linked, both require more cybersecurity measures. It’s crucial to have a cyber simulation program that prepares IT and ICS security teams to defend against cyber threats and accommodates their different organizational structures and objectives.
The number of cybersecurity incidents in OT environments has been rising, which is why forward-thinking organizations are being proactive in preparing for an ICS or cyber-physical incident. The cost of an OT attack averages $3 million, but many cost more, with some companies reporting ICS incident costs of over $100 million. Plus, the repercussions go beyond anything monetary, affecting people’s lives – an OT incident may mean loss of power, the inability to fulfill pharmaceutical orders, or other significant disruptions to business, manufacturing, and shipping.
By 2025, Gartner predicts that cyber attackers will have weaponized OT environments to successfully harm or kill people.
ICS security teams should be able to quickly detect and respond to the various forms of cyberattacks and know how to mitigate risk. They need to understand attack flows, what ingress points are susceptible to an attack, how to respond if a system is compromised, and how to limit cyber-physical damage. OT incident response (IR) teams also need to know what actions they should NOT take, and when they are relying too much on IT monitoring and protocols. A live-fire, hyper-realistic cyber range program for OT teams, like Cloud Range’s OT cyber simulation training, allows OT IR and ICS security teams to practice their skills, hone their abilities, and identify any gaps, so they are measurably ready to defend against the latest threats.
Cloud Range’s cybersecurity training solutions also improve communication and decision-making. For example, no company wants to find out that a warning sign was registered as a false positive or that an alert was ignored because each team thought another team was responding. Cloud Range’s scenarios help enhance teamwork, technical proficiency, collaboration, report-writing, critical thinking, and other technical and soft skills. Our mission debriefs and surveys show that our customers see quantifiable development across the board and that response times are shortened. That helps ensure that IT and ICS security teams can speak the same language, recognize signs of a potential cyberattack, prevent writing something off as a false positive, and minimize the effects of any threats.
Proactive, live-fire cyber simulation practice for teams is extremely effective in reducing risk. Cloud Range’s advanced, hyper-realistic cyber range program trains security professionals to better fortify and defend IT and OT environments and work better together to address incidents. The result is end-to-end cyber risk management.
Ready to upskill your cyber defenders? Contact us to learn about our award-winning cyber simulation program.
---
Founder and CEO of Cloud Range, Debbie Gordon is a globally recognized entrepreneur leading a new category in cybersecurity. Cloud Range was founded on the premise of closing the cybersecurity skills gap by giving security teams the ability to gain real-life experience and practice defending against live cyber attacks in a protected customized dynamic environment. A consummate entrepreneur, Debbie began her career 25+ years ago in the technical education/certification space and has since built and sold several companies in eCommerce, IT asset management, and training.
Photo by Loïc Manegariuim from Pexels